공지사항
업데이트 내역, 신제품/이벤트 소식 등 다양한 정보를 제공합니다.
As of June 27, 2017, the distribution of Petya Ransomware to the world has caused many damages to corporations and individuals. The Ransomware is utilizing same SMB vulnerability used to spread the WannyCry Ransomware, propagating is fast and wide.
The start of the distribution of Petya Ransomware began to spread through certain well-known software update servers in Ukraine, which is spreading through the SMBv1 protocol's EternalBlue vulnerability. In particular, Petya Ransomware includes the behavior Master Boot Record (MBR) modification in addition to file encryption interfering the system boot by displaying the message.
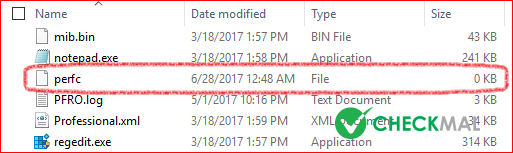
By analyzing the behavior after the infection, the Petya Ransomware utilizes WMI function creates zero byte "C:\Windows\perfc" by executing rundll.32 "C:\Windows\perfc.dat" #1, preventing encryption to run again.
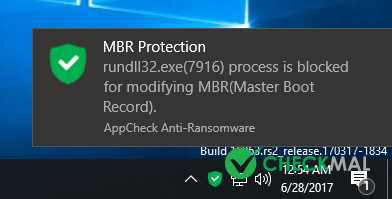
The MBR modification results to display fake CHKDSK message and Ransomware message, AppCheck Pro blocks the behavior as follows.
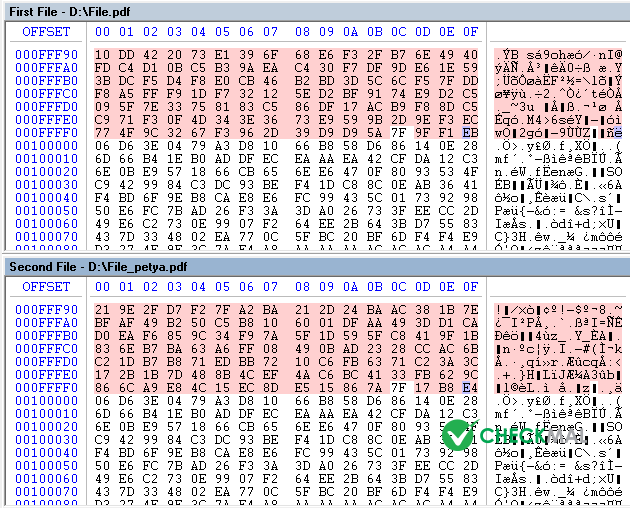
If MBR modification is not blocked, following files are encrypted with AES-128 without modification of filename nor file extension. ".3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx, .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py, .pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xvd, .zip"
If target file size is more than 1MB, encryption is run partially from file offset 0x0~0xFFFFF.
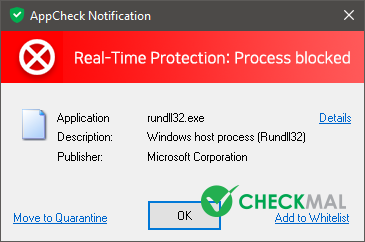
AppCheck Anti-Ransomware protects file encryption and roll-back the change of the encryption.
After the encryption, Petya Ransomware tries to propagating to local network using network shared folder and SMB vulnerabilities.
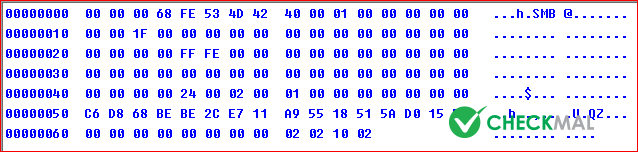
After the infection and MBR modification has completed, Petya Ransomware adds the command to reboot system after 1 hour. "schtasks /Create /SC once /TN "" /TR "C:\Windows\system32\shutdown.exe /r /f" /ST <Specific Time>"
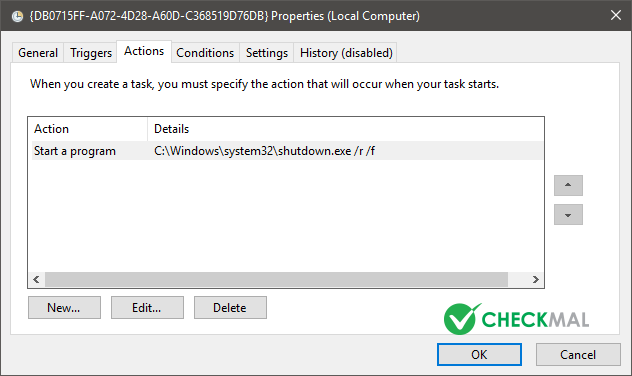
When system reboots automatically, displays fake "CHKDSK" screen, disguising that system had a disk problem.
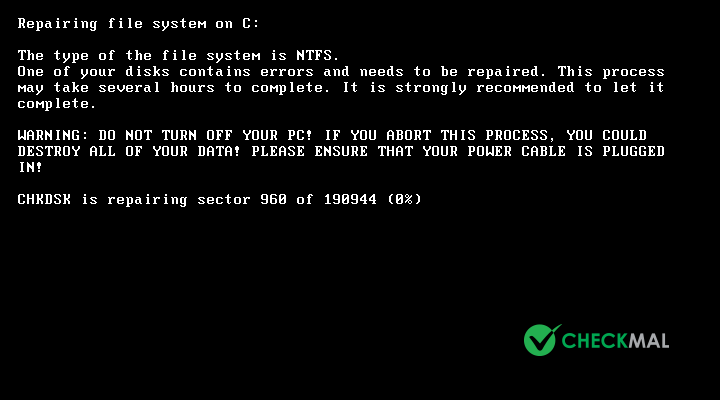
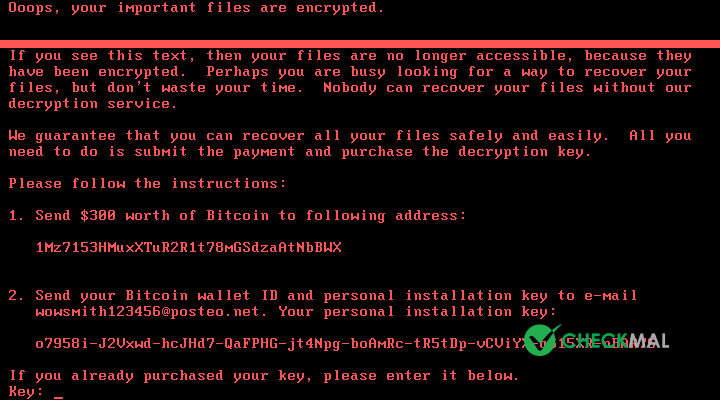
After the CHKDSK completes, payment information is displayed, requiring $300 USD Bitcoin and guides to send personal installation key to specified email.
Due to a series of Petya Ransomware infections, users may have difficulty recovering from system booting failure and loosing personal data files such as documents and photos stored in the system for not paying for the decryption. Especially, corporate environment is warned where internal network is used for the propagation through SMB vulnerability, the whole systems connected to network may be damaged by single infection.
Please be noticed Microsoft has already announced the MS17-010 security patch in March 2017, regarding the SMB vulnerability. Also latest security patch can be updated through Windows Update for all Windows versions including outdated Windows XP, Vista, 8, Server 2003 versions.
AppCheck Free version does not includes MBR Protection, it is recommended to upgrade to AppCheck Pro for better protection.
The start of the distribution of Petya Ransomware began to spread through certain well-known software update servers in Ukraine, which is spreading through the SMBv1 protocol's EternalBlue vulnerability. In particular, Petya Ransomware includes the behavior Master Boot Record (MBR) modification in addition to file encryption interfering the system boot by displaying the message.
By analyzing the behavior after the infection, the Petya Ransomware utilizes WMI function creates zero byte "C:\Windows\perfc" by executing rundll.32 "C:\Windows\perfc.dat" #1, preventing encryption to run again.

The MBR modification results to display fake CHKDSK message and Ransomware message, AppCheck Pro blocks the behavior as follows.

If MBR modification is not blocked, following files are encrypted with AES-128 without modification of filename nor file extension. ".3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx, .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py, .pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xvd, .zip"
If target file size is more than 1MB, encryption is run partially from file offset 0x0~0xFFFFF.

AppCheck Anti-Ransomware protects file encryption and roll-back the change of the encryption.

After the encryption, Petya Ransomware tries to propagating to local network using network shared folder and SMB vulnerabilities.

After the infection and MBR modification has completed, Petya Ransomware adds the command to reboot system after 1 hour. "schtasks /Create /SC once /TN "" /TR "C:\Windows\system32\shutdown.exe /r /f" /ST <Specific Time>"

When system reboots automatically, displays fake "CHKDSK" screen, disguising that system had a disk problem.

After the CHKDSK completes, payment information is displayed, requiring $300 USD Bitcoin and guides to send personal installation key to specified email.

Due to a series of Petya Ransomware infections, users may have difficulty recovering from system booting failure and loosing personal data files such as documents and photos stored in the system for not paying for the decryption. Especially, corporate environment is warned where internal network is used for the propagation through SMB vulnerability, the whole systems connected to network may be damaged by single infection.
Please be noticed Microsoft has already announced the MS17-010 security patch in March 2017, regarding the SMB vulnerability. Also latest security patch can be updated through Windows Update for all Windows versions including outdated Windows XP, Vista, 8, Server 2003 versions.
AppCheck Free version does not includes MBR Protection, it is recommended to upgrade to AppCheck Pro for better protection.
