Notice
Various information is provided including new products, AppCheck update details, and event information.
Updated: May.14.2017 18:39
- Install patch in following url.
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- If you are unable to install patch, you may do following.
1. Block SMB related port in windows firewall: 137(UDP), 138(UDP), 139(TCP), 445(TCP)
2. Disable SMB Protocol:
- For Windows Vista or Windows Server 2008 or higher
----
WannaCry Ransomware is distributed around the world on May 12, 2017, and attention is required. WannaCry (aka, WannaCryptor or WCry) Ransomware is targeting to Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012 R2, Windows RT 8.1, Windows 10, Windows Server 2016, without the patch of MS17-010.
Especially, the propagation is worm type, utilizing ETERNALBLUE vulnerability. Without MS17-010 security patch from Microsoft regular security update in March 2017, the damage is highly expected.
The security vulnerability was utilized by NSA and released to the public by Shadow Brokers hacking group. If the patch is not applied, an attacker may remotely execute the code by sending a specially crafted message to the Windows SMBv1 server. (CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, CVE-2017-0148)
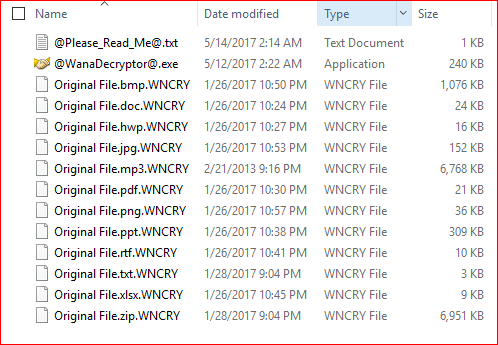
When the code is executed, personal data files such as documents, pictures, videos, music, and compressed files are encrypted to ".WNCRYT" extension and make final changes to ".WNCRY" extension.
During the process of file encryption, if the following processes are running through the taskdl.exe(SHA-1: 47a9ad4125b6bd7c55e4e7da251e23f089407b8f), the system automatically processes the data so that the related data can be encrypted.
Also executes "icacls . /grant Everyone:F /T /C /Q" command to gain access all folders and files.
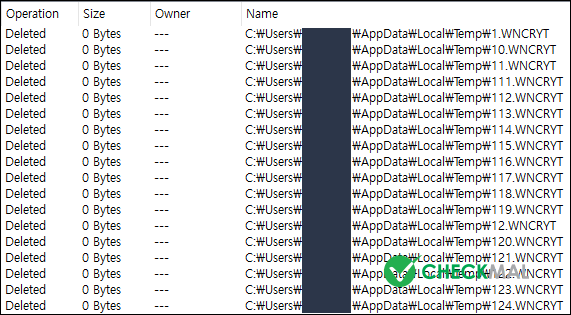
WannaCryptor Ransomware keeps the original file during the encryption process and deletes original files once the encryption process has completed. File created temporarily during the encryption (.WNCRYT) is renamed to <number>.WNCRYT and moved to the temporary folder (%Temp%), then automatically removed.
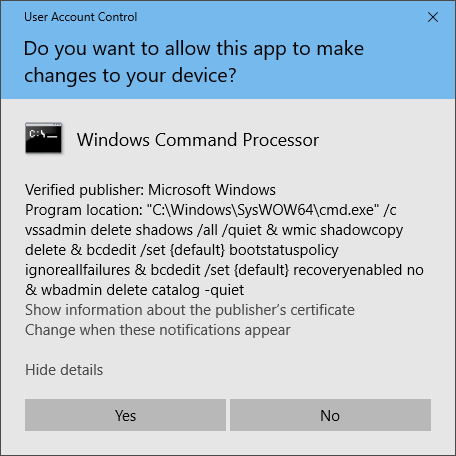
Delete the Volume Shadow Copy Service (VSS) and boot recovery options through the following command to disable the system restore and recovery options after file encryption is complete.
After that, it downloads tor binary and extracts to "C:\Users\%UserName%\AppData\Roaming\tor" for creating "Wana Decrypt0r 2.0" window for communicating through tor network.
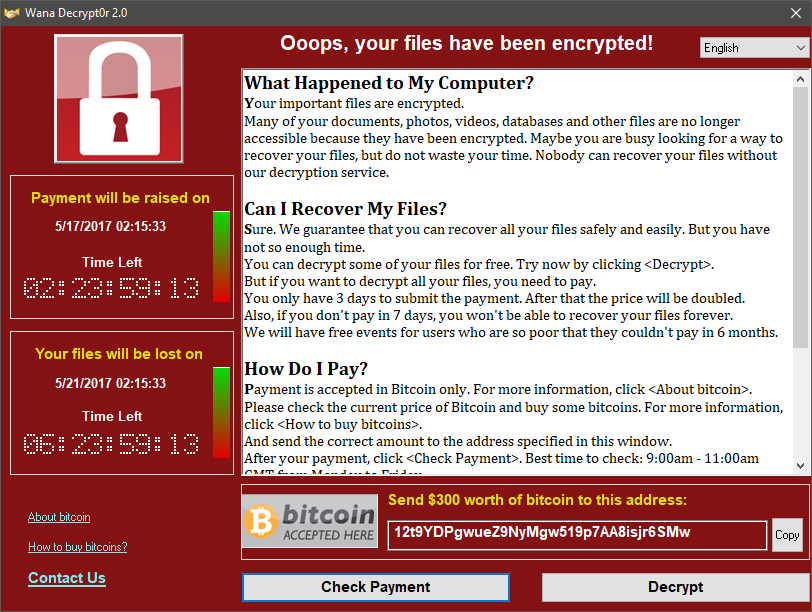
Finally, "Wana Decrypt0r 2.0" message window is displayed in 28 languages, depending on the user's operating system language, guides user to pay within time.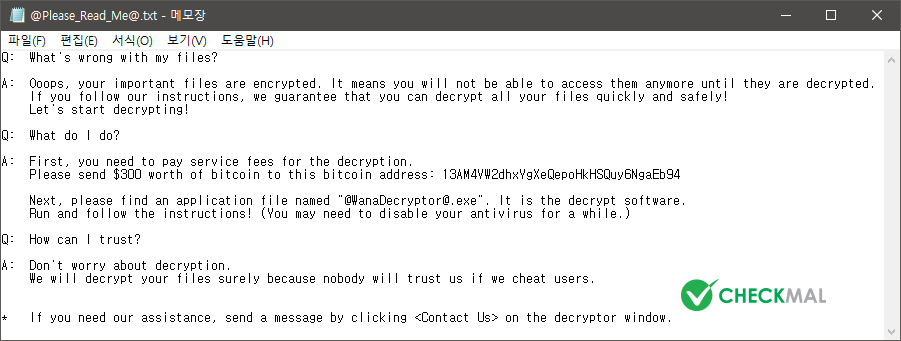
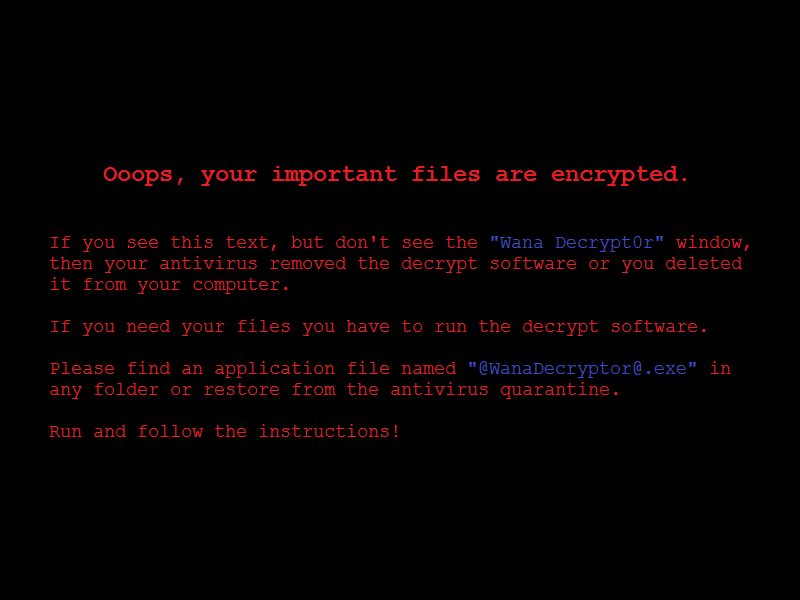
In addition to this, @Please_Read_Me@.txt also stores information for the payment, and changes desktop background to @WanaDecryptor@.bmp image.
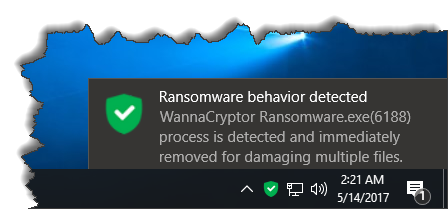
AppCheck Anti-Ransomware protects user data safely by detecting Ransomware's behavior when file encryption is performed due to infection of WannaCryptor Ransomware without any update.
For more information, please refer to the video WannaCryptor Ransomware block video: https://www.checkmal.com/page/resource/video/?detail=read&idx=416&lang=en
Currently, large scale WannaCryptor Ransomware damage occurs in domestic and overseas. Especially, in PC environment where security patch is not applied, BSoD may occur due to vulnerability attack. In this case, block 445 port to block invalid SMB protocol, and apply the security patch.
Related News:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks
https://www.symantec.com/connect/blogs/what-you-need-know-about-wannacry-ransomware
- Install patch in following url.
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- If you are unable to install patch, you may do following.
1. Block SMB related port in windows firewall: 137(UDP), 138(UDP), 139(TCP), 445(TCP)
2. Disable SMB Protocol:
- For Windows Vista or Windows Server 2008 or higher
----
WannaCry Ransomware is distributed around the world on May 12, 2017, and attention is required. WannaCry (aka, WannaCryptor or WCry) Ransomware is targeting to Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012 R2, Windows RT 8.1, Windows 10, Windows Server 2016, without the patch of MS17-010.
Especially, the propagation is worm type, utilizing ETERNALBLUE vulnerability. Without MS17-010 security patch from Microsoft regular security update in March 2017, the damage is highly expected.
The security vulnerability was utilized by NSA and released to the public by Shadow Brokers hacking group. If the patch is not applied, an attacker may remotely execute the code by sending a specially crafted message to the Windows SMBv1 server. (CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, CVE-2017-0148)

When the code is executed, personal data files such as documents, pictures, videos, music, and compressed files are encrypted to ".WNCRYT" extension and make final changes to ".WNCRY" extension.
During the process of file encryption, if the following processes are running through the taskdl.exe(SHA-1: 47a9ad4125b6bd7c55e4e7da251e23f089407b8f), the system automatically processes the data so that the related data can be encrypted.
- taskkill.exe /f /im mysqld.exe
- taskkill.exe /f /im sqlwriter.exe
- taskkill.exe /f /im sqlserver.exe
- taskkill.exe /f /im MSExchange*
- taskkill.exe /f /im Microsoft.Exchange.*
Also executes "icacls . /grant Everyone:F /T /C /Q" command to gain access all folders and files.

WannaCryptor Ransomware keeps the original file during the encryption process and deletes original files once the encryption process has completed. File created temporarily during the encryption (.WNCRYT) is renamed to <number>.WNCRYT and moved to the temporary folder (%Temp%), then automatically removed.

Delete the Volume Shadow Copy Service (VSS) and boot recovery options through the following command to disable the system restore and recovery options after file encryption is complete.
- vssadmin delete shadows /all /quiet
- wmic shadowcopy delete
- bcdedit /set {default} bootstatuspolicy ignoreallfailures
- bcdedit /set {default} recoveryenabled no
- wbadmin delete catalog -quiet
After that, it downloads tor binary and extracts to "C:\Users\%UserName%\AppData\Roaming\tor" for creating "Wana Decrypt0r 2.0" window for communicating through tor network.

Finally, "Wana Decrypt0r 2.0" message window is displayed in 28 languages, depending on the user's operating system language, guides user to pay within time.


In addition to this, @Please_Read_Me@.txt also stores information for the payment, and changes desktop background to @WanaDecryptor@.bmp image.

AppCheck Anti-Ransomware protects user data safely by detecting Ransomware's behavior when file encryption is performed due to infection of WannaCryptor Ransomware without any update.
For more information, please refer to the video WannaCryptor Ransomware block video: https://www.checkmal.com/page/resource/video/?detail=read&idx=416&lang=en
Currently, large scale WannaCryptor Ransomware damage occurs in domestic and overseas. Especially, in PC environment where security patch is not applied, BSoD may occur due to vulnerability attack. In this case, block 445 port to block invalid SMB protocol, and apply the security patch.
Related News:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks
https://www.symantec.com/connect/blogs/what-you-need-know-about-wannacry-ransomware
